A vulnerability assessment is a type of process that involves defining, identifying, classifying, and prioritizing vulnerabilities that can be found among computer systems, specific applications, and network infrastructures. They even provide organizations with relevant knowledge, awareness, and background in order to make them understand with regards to the threat to the environment. The process itself is intended for identifying threats and risks. They make use of several effective automated testing tools in which the results will be reflected in the vulnerability assessment report. Organizations and even individuals who experience cyberattacks can also benefit from a vulnerability assessment. However, large enterprises that are subject to the ongoing attacks will most likely to benefit from a vulnerability analysis.
10+ Vulnerability Assessment Samples
1. Vulnerability Assessment
Vulnerability assessments are designed to provide organizations with a specific information regarding the security weaknesses of the environment. It also guides you on how you are going to assess the risks that is being associated with those weaknesses. This would offer organizations a better understanding of the assets, flaws and risks that will help in reducing cybercriminal instances that will breach the system.
2. Security Vulnerability Assessment
Security vulnerabilities enable various hackers to get into the access of the IT systems including applications. With that, it would be very necessary for most of the organizations including large enterprises to be able to identify their weaknesses before they will get exploited. The use of a vulnerability assessment can even help companies to improve in the security of their own systems.
3. Sample Vulnerability Assessment
4. Network Vulnerability Assessment
5. Climate Vulnerability Assessment
6. Facility Vulnerability Assessment
7. Database Vulnerability Assessment
8. Security Guardium Vulnerability Assessment
9. Vulnerability Assessment Policy
10. Vulnerability Risk Assessment
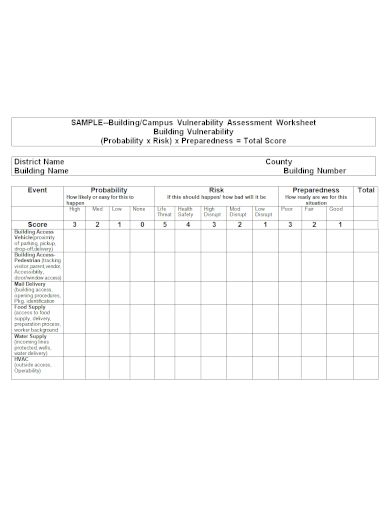
11. Vulnerability Assessment Worksheet
How to Perform a Network Vulnerability Assessment?
Risk Identification and Analysis
This type of process usually starts with the identification of assets that belong to the information system of a certain company. Using the list of the IT equipment, companies are able to start assigning each of these risks to each of the assets. After this, you are going to assign and perform the analysis that help determine the actual risk of each of those assets. When you have already identified this risks and have it analyzed already, the vulnerability assessment process can start shifting its focus on the aspect that has the most amount of risk.
Vulnerability Scanning Policies and Procedures
Those written policies and procedures are considered to be the backbone of every action that has been planned to perform. All activities are preferred to be just within the boundaries of those policies and procedures. You will obtain set of rules that needs to be implemented in order to provide specifications for any forbidden behavior.
Vulnerability Scanning
This is the process wherein you will be identifying security weaknesses in every information systems. It can be performed by most of the technical IT staffs that are well-trained and has the ability to conduct a vulnerability scan.
Configure a Vulnerability Scan
This can be used in the identification of the objectives and the system that you want to scan.
Perform the Scan
After you have determined what system you want to be scanned, you may save the configuration and have it run. It may usually take a few minutes or hours to complete depending on the size of the target set.
Evaluate and Consider some Potential Risks
When you are performing a scan on various systems, always take extra caution. Some links and connections cannot even handle the traffic load that are being generated by the scan itself. Chances would be the remote target would probably shut down and will become unavailable at the time.
Interpretation of the Scan Results
Having a knowledge about the scanned system is very essential especially if you opt to prioritize some remediation efforts. Each of the vulnerability scanning tool prioritize vulnerabilities automatically.
Remediation Process and Mitigation Plan
It is the responsibility of the information security staff to mitigate each of the vulnerability detected and be able to coordinate with the IT staffs to ensure good communication for the mitigation actions. Their communication can help the process more successful and fast.
FAQs
What are the types of vulnerability assessment?
This include external scans, internal scans, and environmental scans.
What are the methodologies of a vulnerability assessment?
It includes initial scanning, scanning, analysis, and remediation.
What are the common vulnerability scanning methods?
It includes network scanning, build assessment, database assessment, and host-based assessment.
Vulnerability assessments should serve as a requisite to most of the organizations in order to maximize the security of the IT infrastructure. This does not only mean protecting the firms from any cyberattacks, but also helping them in building a credible stance and protection to all of their data.
Related Posts
FREE 9+ Sample Needs Assessment Survey
FREE 9+ Sample Assessment Plan
FREE 9+ Sample Property Assessment
FREE 9+ Sample Organizational Assessment
FREE 9+ Sample Self Assessment Forms
FREE 8+ Sample Community Needs Assessment
FREE 7+ Sample Product Risk Assessment
FREE 6+ Sample Training Assessment Forms
FREE 44+ Assessment Forms
FREE 10+ IT Assessment Templates
FREE 10+ Self Assessment Samples
FREE 10+ Sample Risk Assessment Checklist
FREE 9+ Functional Behavior Assessment Samples
FREE 7+ Sample Business Risk Assessment
FREE 7+ Sample Health Assessments