In the modern digital landscape, where information and services are increasingly accessible through online platforms, the need for robust authorization mechanisms has never been more critical. Authorization serves as the gatekeeper that controls who can access what resources, ensuring data security, user privacy, and system integrity. An authorization checklist acts as a comprehensive guide to ensure that access control measures are properly implemented, reducing the risk assessment of unauthorized access and potential breaches.
25+ Authorization Checklist Samples
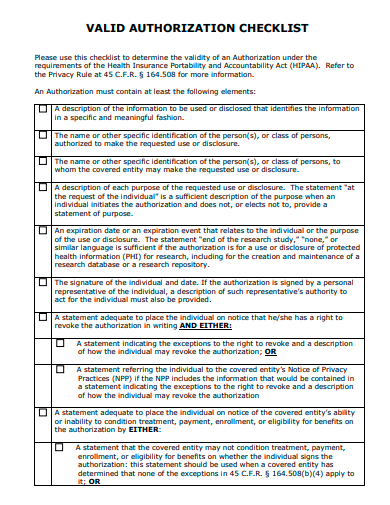
1. Valid Authorization Checklist Template
2. Travel Authorization Checklist Template
3. Prior Authorization Checklist Template
4. Laser Spectator Status Authorization Checklist Template
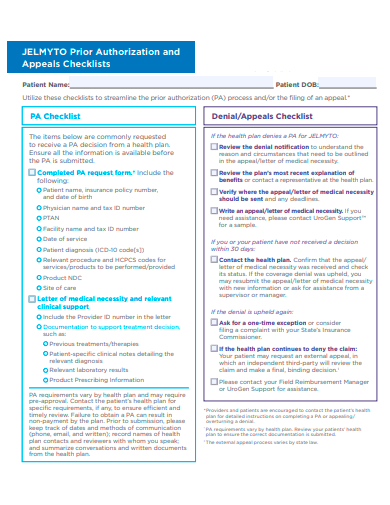
5. Prior Authorization and Appeal Checklist Template
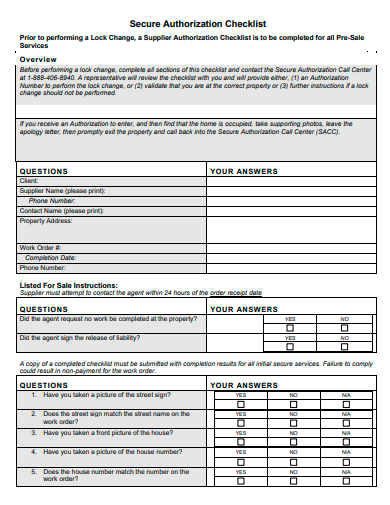
6. Secure Authorization Checklist Template
7. Request For Authorization Checklist Template
8. Sample Authorization Checklist Template
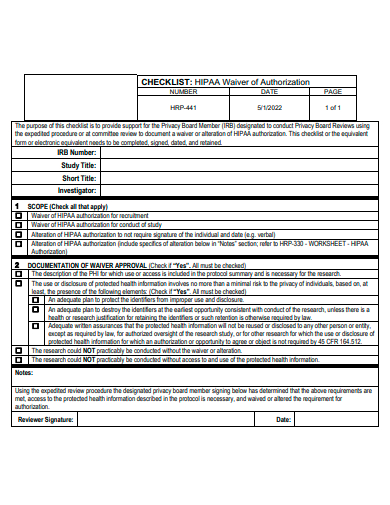
9. HIPPA Authorization Form Checklist Template
10. Temporary Authorization Certificate Checklist Template
11. Authorization Reviewer Checklist Template
12. Basic Authorization Checklist Template
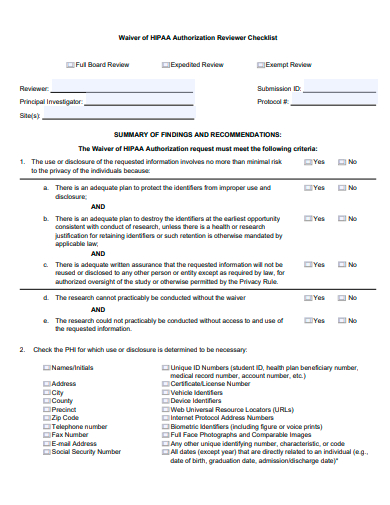
13. Waiver of Authorization Checklist Template
14. Authorization Requirements Reviewers Checklist Template
15. Emergency Authorization Request Checklist Template
16. Program Authorization Checklist Template
17. Home Health Prior Authorization Checklist Template
18. Benefit Verifications and Prior Authorization Checklist Template
19. Validate Authorization Forms Checklist Template
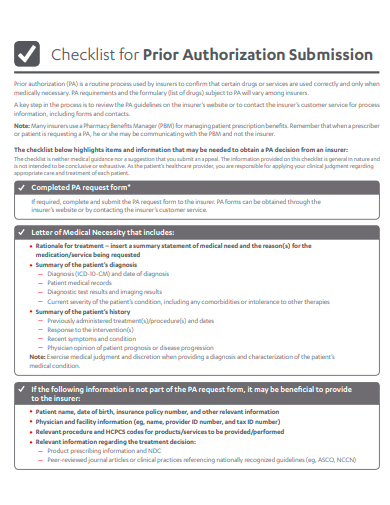
20. Prior Authorization Submission Checklist Template
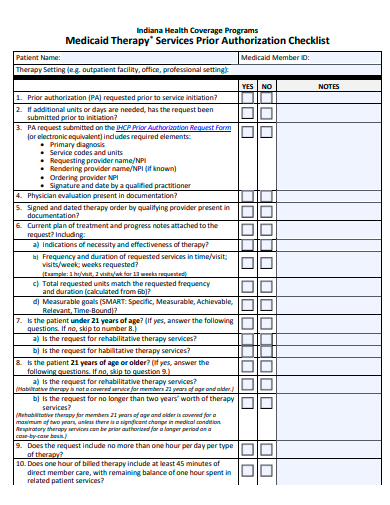
21. Services Prior Authorization Checklist Template
22. Employment Authorization Checklist Template
23. Travel Authorization Reimbursement Request Checklist Template
24. Verification and Authorization Checklist Template
25. Authorization Request Checklist Template
26. Authorization to Issue Checklist Template
What is Authorization Checklist?
An Authorization Checklist is a systematic and organized set of guidelines, policies and procedures, and criteria designed to ensure proper access control and authorization management within a digital or physical environment. It outlines the steps, best practices, and requirements for granting or restricting access to resources, data, system documentation, or physical areas based on predefined roles, permissions, and security policies.
How To Make Authorization Checklist?
An authorization checklist serves as a comprehensive reference for individuals responsible for managing access rights, helping them ensure that only authorized users are granted appropriate levels of access while minimizing the risk of unauthorized or malicious activities. Creating a comprehensive Authorization Checklist involves careful consideration of various access control aspects and security measures. Here’s a step-by-step guide to help you formulate an effective Authorization Checklist for your organization:
Step 1- Identify Stakeholders and Resources
Determine the key stakeholders who will be involved in the access control process. Identify the critical digital resources, systems, databases, physical areas, or applications that require authorization.
Step 2- Define User Roles and Permissions
Clearly define the different user roles within your organization and the specific permissions each role requires. Assign permissions based on the principle of least privilege, ensuring that users only have access to the resources necessary for their job functions.
Step 3-Establish Access Policies
Develop access policies that outline the rules and guidelines for granting and managing access. Specify criteria for requesting access, approval workflows, and any exceptional cases that require special consideration.
Step 4-Implement Authentication Mechanisms
Choose appropriate authentication methods to verify users’ identities before granting access. Consider options such as passwords, multi-factor authentication (MFA), biometrics, or smart cards.
Why is an Authorization Checklist important for businesses?
An Authorization Checklist is crucial for businesses to ensure data security, prevent unauthorized access, maintain compliance with regulations, and foster a culture of security awareness among employees.
How does an Authorization Checklist enhance security?
An Authorization Checklist enhances security by defining access policies, implementing role-based access control, enforcing multi-factor authentication, setting up session management, and maintaining detailed logs. These measures collectively mitigate the risk of unauthorized access and data breaches.
How can an organization determine the appropriate access roles and permissions for users?
Organizations can determine access roles and permissions by conducting a thorough analysis of job functions and responsibilities. Collaboration with department heads and employees can help define the necessary levels of access required for each role.
In the digital age, where unauthorized access and data breaches pose significant threats, an authorization checklist is an indispensable tool for organizations to enhance security and safeguard sensitive information. By outlining access policies, adhering to the principle of least privilege, implementing multi-factor authentication, managing user sessions, maintaining comprehensive logs, conducting access reviews, and prioritizing encryption, organizations can create a robust access control framework.
Related Posts
FREE 18+ Complaint Checklist Samples in MS Word | Google Sheets | PDF
FREE 18+ Internship Checklist Samples in MS Word | Google Docs | PDF
FREE 18+ Statement Checklist Samples in MS Word | Google Sheets | PDF
FREE 20+ Voluntary Checklist Samples in MS Word | Google Sheets | PDF
FREE 18+ Summary Checklist Samples in MS Word | Google Sheets | PDF
FREE 14+ Sponsorship Checklist Samples in MS Word | MS Excel | PDF
FREE 18+ Conference Checklist Samples in MS Word | Google Sheets | PDF
FREE 17+ Lesson Checklist Samples in MS Word | Google Sheets | PDF
FREE 18+ Progress Checklist Samples in MS Word | Google Docs | PDF
FREE 18+ Enrollment Checklist Samples in MS Word | Google Docs | PDF
FREE 18+ Graduation Checklist Samples in MS Word | Google Sheets | PDF
FREE 15+ Consent Checklist Samples in MS Word | Google Sheets | PDF
FREE 18+ Review Checklist Samples in MS Word | Apple Pages | PDF
FREE 18+ Submission Checklist Samples in MS Word | Google Docs | PDF
FREE 18+ Request Checklist Samples in MS Word | MS Excel | PDF