According to A. Swetha and Y. Latha, if not properly secured, the public Internet and eCommerce, as well as private PCs and computer networks, are becoming increasingly vulnerable to destructive attacks. Hackers, viruses, vengeful employees, and even human error are all potential threats to networks. Any business owner whose network connects to the outside world faces the risk of losing irreplaceable data. Employees with remote access and Internet access may be able to communicate in ways you never anticipated. Access to the Internet can open up a whole new world of possibilities for connecting with customers and vendors, as well as providing a wealth of information. However, these same opportunities make a local area network (LAN) vulnerable to theft and vandalism.
One of the fastest-growing types of criminal conduct is cybercrime. By 2021, the global cost of repairing the damage caused by cybercrime is expected to reach $6 trillion, more than twice the cost in 2015. The average cost of a cyberattack, according to some reports, is more than $1 million, and this figure is anticipated to climb.
It’s more critical than ever for you as a managed services provider (MSP) to guarantee that your customers have the greatest network security possible. Unfortunately, hackers and cyber attackers are persistent and cunning, so you’ll need to use networking security technologies to set up and maintain a strong line of protection.
10+ Network Security Proposal Samples
1. Network and Information Security Proposal
2. Network Security Thesis Proposal
3. Network Security Assessment Proposal
4. Network Security Request for Proposal
5. Network Security Services Proposal
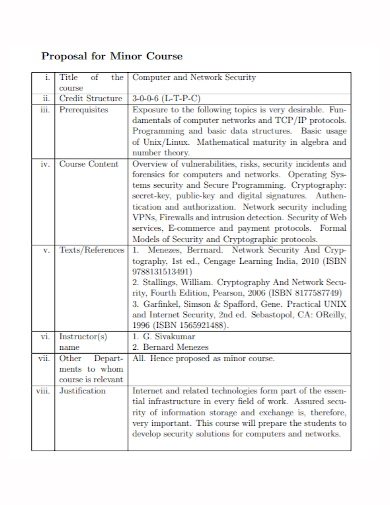
6. Network Security Course Proposal
7. Network Security Call for Proposal
8. Network Analysis Security Proposal
9. Network Security Testing Proposal
10. Network Discovery Security Proposal
11. Network Access Control Security Proposal
The many countermeasures put in place to secure the network and the data stored on or traveling over it are referred to as network security. The goal of network security is to protect the network against cyberattacks, hacker attempts, and employee errors. Hardware, software, and cloud services are the three components of network security.
Developing Network Security Proposal
- Identify the assets and the threats – Identifying the assets you want to safeguard is the first step in creating a cybersecurity plan. This stage entails taking into account the context of your company, as well as asset/risk assessment and threat management systems.
- Prioritize the assets, risks, and threats – Following an assessment of your assets, threats, and risks, the next step is to prioritize them using the appropriate approach for your organization’s setting. To assist you to identify high risks, answer the following three questions: What are the dangers or challenges that your company faces? What are your company’s primary worries when it comes to cybersecurity? Which dangers and threats would be the most damaging to your company? After that, you can decide on countermeasures and therapies for each danger or hazard you’ve discovered. Sort them from easiest to most difficult to obtain.
- Set goals – It’s fine to set lofty goals, but achieving them is more vital to your firm than a long list of ineffective policies and procedures. While a cybersecurity plan should include all activities you want to do, it’s also important to establish genuinely attainable goals. Begin with the basics: goals that are simple to achieve. Remember that cybersecurity rules are the bedrock upon which the rest of your cybersecurity initiatives will be built. Focus first on the most critical and high-risk areas, and get them out of the way since they are the most vital.
- Document cybersecurity policies – It’s a well-known fact that small businesses rely on word-of-mouth and intuitive understanding more than they do on the books. It’s critical to document your protocols, processes, policies, and procedures in the field of cybersecurity. Having a cybersecurity plan gives you access to a comprehensive toolset that follows cybersecurity best practices and rules. Although developing these regulations may seem like a daunting undertaking, some organizations are acknowledged for their technical and business writing ability. Any of these companies can provide you with services.
- Link your goals to your business objectives – Determine the business rationale for each of the previously mentioned objectives. It’s preferable, for example, to state that a firewall is required not only for the sake of having one but so that employees may quickly access the data they need to complete their jobs. Don’t overlook the business aspects of your cybersecurity strategy, as each of your plans will have an impact on your company.
- Test for vulnerabilities – After you’ve completed everything, don’t forget to give it a try. You must determine whether or not your cybersecurity strategy is effective. It will be too late and too dangerous to wait until a cybercrime has occurred. As a result, put your strategy to the test. How do you go about doing this? Hire a cybersecurity specialist to undertake a thorough security audit at least once a year to ensure that your plan is still relevant, up to date, and effective. Some businesses even engage ethical hackers to try to break into their systems. Because cyber-threats are continually changing, your computer security strategy should as well.
FAQs
What are the components of network security?
We have the hardware, software, and cloud services. Within the networking context, hardware appliances are servers or devices that fulfill particular security duties. To provide further detection and threat remediation, network security software, which includes antivirus apps, can be installed on devices and nodes across the network. Offloading infrastructure to a cloud provider is referred to as cloud services. The setup is identical to how network traffic goes through in-line hardware appliances, with the exception that incoming network traffic is diverted to the cloud service.
Who is usually in charge when it comes to security reports?
The front office of the security company is normally in charge of designing and finalizing the security proposal. Because they know more about security than anyone else.
It is not necessary to be a computer expert to create a cybersecurity plan or policy. Technical writing, on the other hand, necessitates the involvement of experts. If you want to see more samples and formats, check out some network security proposal samples and templates provided in the article for your reference.
Related Posts
Title Project Proposal Samples [ Community, School, Student ]
FREE 10+ Product Supply Proposal Samples in MS Word | Google Docs | Apple Pages | PDF
FREE 10+ Health Project Proposal Samples [ Public, Mental, Healthcare ]
FREE 11+ Engineering Project Proposal Samples in PDF | MS Word
FREE 4+ Racing Sponsorship Proposal Samples [ Team, Car, Driver ]
FREE 10+ Nursing Project Proposal Samples [ Community, Health, Clinical ]
FREE 11+ Student Council Proposal Samples in PDF | DOC
FREE 10+ Facilities Management Proposal Samples in MS Word | Google Docs | Apple Pages | PDF
FREE 8+ Joint Venture Proposal Samples [ Commercial, Real Estate, Construction ]
FREE 10+ Scholarship Proposal Samples [ Project, Grant, Sponsorship ]
FREE 10+ Computer Purchase Proposal Samples in MS Word | Google Docs | Apple Pages | PDF
FREE 10+ Network Project Proposal Samples [ Design, Security, Bank ]
FREE 14+ Accounting Proposal Samples in PDF | MS Word
FREE 10+ Church Event Proposal Samples in MS Word | Google Docs | Apple Pages | PDF
FREE 10+ History Proposal Samples [ Dissertation, Thesis, Paper ]