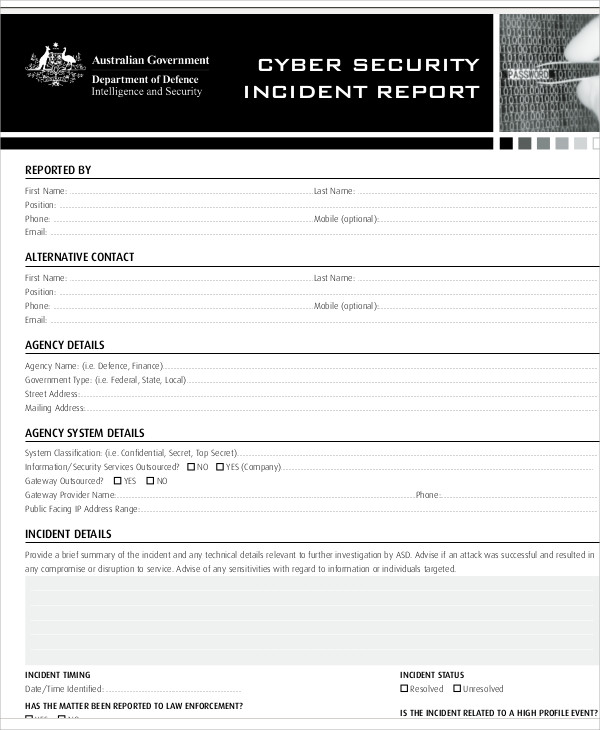
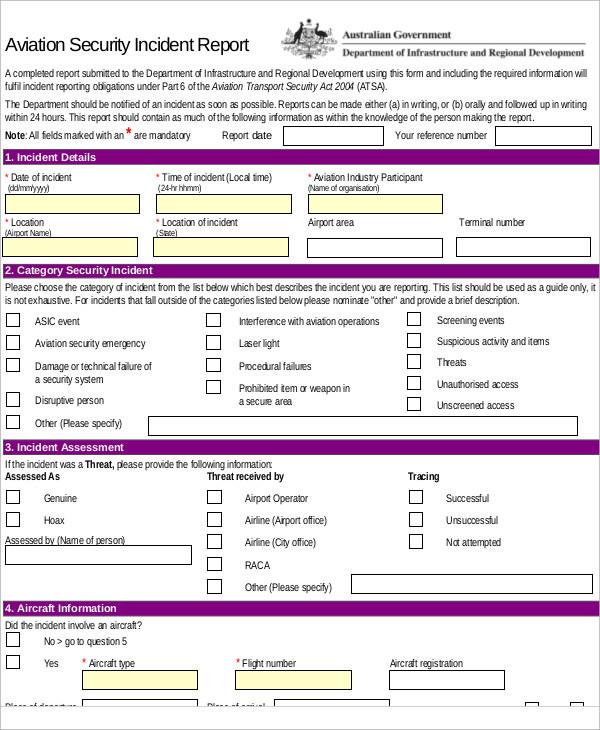
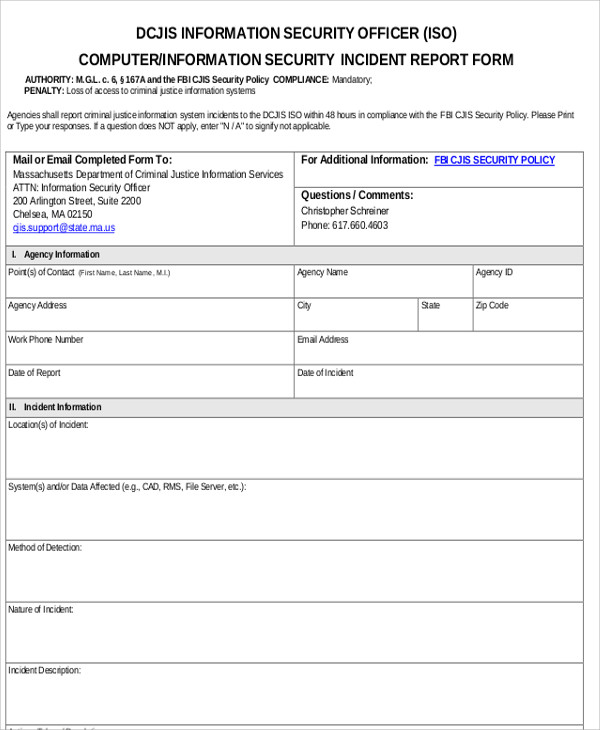
Security incident reports are made by most establishments to record details of serious incidents that happen within and around the vicinity of establishments. These include campus grounds, stores, malls, and company premises. Events that require security incident reports range from less serious offenses such as loitering and entering without permission to serious incidents like theft, physical assault, damage to property, and even murder or homicide.

Download Security Incident Reports Bundle
Cyber Incident Reporting Requirements
Introduction
Cyber incident reporting is a critical component of an organization’s cybersecurity strategy. It ensures timely identification, response, and mitigation of cyber threats, while also enabling organizations to comply with legal and regulatory obligations. This report outlines the key requirements for cyber incident reporting, including who must report, what must be reported, when reports must be made, and how the reporting process should be conducted.
1. Who Must Report
- Organizations: Any entity that handles sensitive or personal data, including businesses, government agencies, healthcare providers, financial institutions, and educational institutions.
- Individuals: Employees, contractors, and other stakeholders who are involved in the handling of sensitive data or who might detect a cyber incident.
2. What Must Be Reported
- Type of Incident: Details of the cyber incident, including whether it is a data breach, malware attack, phishing attempt, denial of service attack, or another type of cyber threat.
- Scope of Impact: The extent of the impact, including the number of individuals affected, the systems compromised, and the data potentially exposed.
- Incident Description: A detailed description of the incident, including how it was detected, the methods used by the attacker, and any vulnerabilities exploited.
- Mitigation Actions: Steps taken to mitigate the incident, including immediate responses, containment measures, and long-term solutions to prevent recurrence.
3. When to Report
- Immediate Reporting: Some incidents, particularly those involving significant data breaches or critical infrastructure, may require immediate reporting within hours of detection.
- Timely Reporting: Most incidents should be reported within a defined timeframe, typically ranging from 24 to 72 hours after detection, depending on the severity and regulatory requirements.
- Ongoing Updates: Continuous updates may be required as new information becomes available and as the incident response progresses.
4. How to Report
- Internal Reporting: Incidents should be reported to internal stakeholders, including the IT department, security teams, and senior management, using predefined channels and protocols.
- External Reporting: Reports should be submitted to relevant external bodies, such as regulatory authorities, law enforcement agencies, and industry-specific organizations. This may include the use of standardized reporting forms and secure communication channels.
- Documentation: Maintain thorough documentation of the incident, including all actions taken, communications, and lessons learned, to support compliance and improve future incident responses.
5. Legal and Regulatory Compliance
- Regulatory Requirements: Organizations must comply with specific reporting requirements set by industry regulations, such as the General Data Protection Regulation (GDPR), Health Insurance Portability and Accountability Act (HIPAA), and the Cybersecurity Information Sharing Act (CISA).
- Industry Standards: Adherence to industry standards and best practices, such as those outlined by the National Institute of Standards and Technology (NIST) and the International Organization for Standardization (ISO), is essential for effective incident reporting.
6. Best Practices
- Incident Response Plan: Develop and maintain a comprehensive incident response plan that includes clear reporting procedures.
- Training and Awareness: Regularly train employees and stakeholders on recognizing and reporting cyber incidents.
- Continuous Improvement: Review and update reporting protocols based on past incidents and emerging threats to enhance the effectiveness of the incident response process.
Conclusion
Effective cyber incident reporting is crucial for minimizing the impact of cyber threats and ensuring organizational resilience. By understanding and adhering to reporting requirements, organizations can improve their cybersecurity posture and comply with legal obligations, thereby protecting sensitive data and maintaining stakeholder trust.

Security Incident Reporting Army Training
Introduction
Effective security incident reporting is critical for maintaining operational security and ensuring quick response to potential threats within the Army. This report outlines the training requirements for Army personnel on security incident reporting, covering the objectives, training content, methodologies, evaluation, and ongoing improvement measures.
1. Objectives of Security Incident Reporting Training
- Awareness: Increase awareness among Army personnel about the importance of timely and accurate security incident reporting.
- Procedures: Educate personnel on the proper procedures for reporting security incidents.
- Compliance: Ensure compliance with Army regulations and standards regarding incident reporting.
- Response: Enhance the ability of personnel to respond swiftly and appropriately to security incidents.
2. Training Content
- Definition of Security Incidents: Understanding what constitutes a security incident, including unauthorized access, data breaches, physical security breaches, and other potential threats.
- Reporting Procedures: Detailed steps on how to report an incident, including the use of specific forms, communication channels, and hierarchical reporting structures.
- Types of Information to Report: Guidance on what information should be included in an incident report, such as the nature of the incident, affected systems or data, time of occurrence, and any immediate actions taken.
- Incident Response Plan: Overview of the Army’s incident response plan, including roles and responsibilities, escalation procedures, and coordination with relevant units and external agencies.
- Confidentiality and Data Protection: Emphasizing the importance of maintaining confidentiality and protecting sensitive information during the reporting process.
- Real-life Scenarios: Case studies and hypothetical scenarios to illustrate common security incidents and appropriate reporting responses.
3. Training Methodologies
- Classroom Instruction: Formal training sessions conducted by qualified instructors to cover the theoretical aspects of incident reporting.
- Hands-on Exercises: Practical exercises and simulations to provide personnel with real-world experience in identifying and reporting security incidents.
- E-Learning Modules: Online training modules to allow flexible learning opportunities and reinforce key concepts.
- Workshops and Seminars: Interactive workshops and seminars to facilitate discussion and knowledge sharing among personnel.
- Assessment and Testing: Regular assessments and tests to evaluate the understanding and retention of incident reporting procedures.
4. Evaluation and Feedback
- Pre-Training Assessment: Assessing the initial knowledge level of personnel before training to tailor the content to their needs.
- Post-Training Evaluation: Conducting evaluations immediately after training sessions to measure the effectiveness and identify areas for improvement.
- Continuous Monitoring: Ongoing monitoring of incident reporting practices to ensure adherence to training and identify any gaps or issues.
- Feedback Mechanisms: Collecting feedback from participants to understand their experience and gather suggestions for enhancing the training program.
5. Ongoing Improvement Measures
- Regular Updates: Continuously updating training materials to reflect changes in Army policies, technological advancements, and emerging threats.
- Refresher Courses: Providing periodic refresher courses to reinforce knowledge and keep personnel up-to-date with the latest reporting procedures.
- Incident Analysis: Analyzing reported incidents to identify trends, common issues, and areas for additional training focus.
- Collaboration: Encouraging collaboration and knowledge sharing among different units to improve overall incident reporting and response capabilities.
Conclusion
The security incident reporting training for Army personnel is essential for maintaining a robust security posture and ensuring quick and effective response to potential threats. By implementing comprehensive training programs, the Army can enhance the awareness, skills, and compliance of its personnel, thereby safeguarding its operations and assets.

Us-Cert Incident Reporting Timelines
Introduction
The United States Computer Emergency Readiness Team (US-CERT) plays a crucial role in the nation’s cybersecurity framework by providing timely and actionable information to protect against cyber threats. Reporting cyber incidents to US-CERT is essential for national security, enabling a coordinated response to mitigate and prevent further damage. This report outlines the key incident reporting timelines and requirements for organizations to comply with US-CERT guidelines.
1. Reporting Categories and Timelines
US-CERT categorizes incidents based on their severity and potential impact. Each category has specific reporting timelines to ensure prompt and appropriate responses.
1.1. Category 1: Emergency (Critical Infrastructure)
- Definition: Incidents that pose an immediate threat to critical infrastructure, national security, or public health and safety.
- Reporting Timeline: Within 1 hour of detection.
- Examples: Large-scale denial of service attacks, significant data breaches affecting critical infrastructure, and malware infections on systems controlling critical operations.
1.2. Category 2: Significant Incident
- Definition: Incidents that have a significant impact on an organization’s operations or pose a substantial threat to national security or public confidence.
- Reporting Timeline: Within 2 hours of detection.
- Examples: Targeted cyberattacks on major financial institutions, widespread ransomware attacks, and breaches involving sensitive government data.
1.3. Category 3: Moderate Incident
- Definition: Incidents that have a moderate impact on an organization’s operations but do not pose an immediate threat to national security or critical infrastructure.
- Reporting Timeline: Within 4 hours of detection.
- Examples: Unauthorized access to non-critical systems, phishing campaigns that do not result in significant data loss, and malware infections on non-critical systems.
1.4. Category 4: Minor Incident
- Definition: Incidents that have a minor impact on an organization’s operations and do not pose a threat to national security or critical infrastructure.
- Reporting Timeline: Within 24 hours of detection.
- Examples: Low-level malware infections, unsuccessful phishing attempts, and minor data breaches involving non-sensitive information.
1.5. Category 5: Ongoing Malicious Activity
- Definition: Incidents involving ongoing malicious activity that has not yet caused significant damage but could escalate if not addressed.
- Reporting Timeline: Within 1 hour of detection.
- Examples: Detection of advanced persistent threats (APTs) or indicators of compromise (IOCs) suggesting a potential larger attack.
2. Reporting Process
2.1. Initial Notification
- Content: Initial reports should include basic information about the incident, such as the type of incident, affected systems, and initial assessment of impact.
- Method: Submit the report through US-CERT’s online reporting portal, email, or phone.
2.2. Follow-Up Reports
- Content: Provide detailed information as it becomes available, including root cause analysis, mitigation actions taken, and any further impact assessment.
- Frequency: Continuous updates should be provided as new information is discovered and the situation evolves.
3. Legal and Regulatory Compliance
- Federal Agencies: Must comply with the Federal Information Security Modernization Act (FISMA) reporting requirements and coordinate with the Department of Homeland Security (DHS) and other relevant agencies.
- Private Sector: While reporting is generally voluntary, compliance with US-CERT guidelines can enhance an organization’s cybersecurity posture and support national security efforts.
4. Best Practices
- Preparedness: Develop and maintain an incident response plan that includes procedures for reporting to US-CERT.
- Training: Regularly train employees on recognizing and reporting cyber incidents.
- Communication: Establish clear lines of communication with US-CERT and other relevant authorities to facilitate timely reporting and response.
Conclusion
Timely and accurate reporting of cyber incidents to US-CERT is vital for national cybersecurity. Adhering to the established timelines and processes ensures a coordinated response, minimizing the impact of cyber threats and enhancing the overall security posture of organizations and the nation.

Best Security Incident Reports
Introduction
Security incident reports are essential tools for documenting and responding to security breaches and threats. A well-structured report provides a clear and detailed account of the incident, helping organizations understand the cause, impact, and necessary corrective actions. This report outlines the best practices for creating effective security incident reports, focusing on structure, content, and process.
1. Structure of a Security Incident Report
A comprehensive security incident report should include the following sections:
- Title Page: Includes the title of the report, the date of the report, and the name of the person or team responsible for the report.
- Executive Summary: A brief overview of the incident, key findings, and actions taken.
- Incident Description: Detailed account of the incident, including what happened, how it was detected, and the timeline of events.
- Impact Analysis: Assessment of the impact on the organization, including affected systems, data, and operations.
- Root Cause Analysis: Identification of the underlying cause(s) of the incident.
- Response Actions: Steps taken to mitigate the incident and restore normal operations.
- Lessons Learned: Insights gained from the incident and recommendations for preventing future incidents.
- Appendices: Supporting documents, logs, and other relevant information.
2. Key Content Elements
Each section of the report should contain specific details to ensure clarity and completeness:
- Executive Summary:
- Brief description of the incident
- Key impacts and affected areas
- Major response actions
- High-level recommendations
- Incident Description:
- Date and time of the incident
- How the incident was discovered
- Detailed sequence of events
- Identification of affected systems and data
- Impact Analysis:
- Extent of the damage (e.g., data loss, system downtime)
- Impact on business operations and services
- Legal and regulatory implications
- Financial impact (if applicable)
- Root Cause Analysis:
- Methods used to determine the root cause
- Detailed explanation of the cause(s)
- Contributing factors
- Response Actions:
- Immediate containment measures
- Eradication steps to remove threats
- Recovery procedures to restore systems
- Communication with stakeholders (internal and external)
- Lessons Learned:
- Analysis of what was done well and what could be improved
- Recommendations for enhancing security measures
- Training and awareness initiatives
- Policy and procedure updates
- Appendices:
- Incident logs and screenshots
- Communication records
- Technical analysis reports
- Relevant policies and procedures
3. Process for Creating Security Incident Reports
Implementing a structured process for creating security incident reports helps ensure consistency and thoroughness:
- Incident Detection: Use monitoring tools and techniques to promptly detect and log security incidents.
- Initial Assessment: Perform an initial assessment to understand the scope and impact of the incident.
- Documentation: Start documenting the incident as soon as it is detected, capturing all relevant details and actions taken.
- Investigation: Conduct a thorough investigation to determine the root cause and impact.
- Reporting: Compile the findings into a structured report using the outlined format.
- Review: Have the report reviewed by key stakeholders, including IT, security, legal, and executive teams.
- Distribution: Distribute the report to relevant parties, ensuring confidentiality and compliance with policies.
- Follow-Up: Implement recommendations and follow up on any outstanding issues or actions.
Conclusion
Creating effective security incident reports is crucial for understanding and mitigating security incidents. By following best practices in structure, content, and process, organizations can enhance their incident response capabilities, improve security posture, and comply with regulatory requirements. Regularly reviewing and updating reporting procedures ensures continuous improvement and preparedness for future incidents.

Browse More Templates On Security Incident Reports
Security Incident Report Template

Security Assessment Report Template

Security Guard Incident Report Template

Construction Security Incident Report Template

How To Write a Security Incident Report?
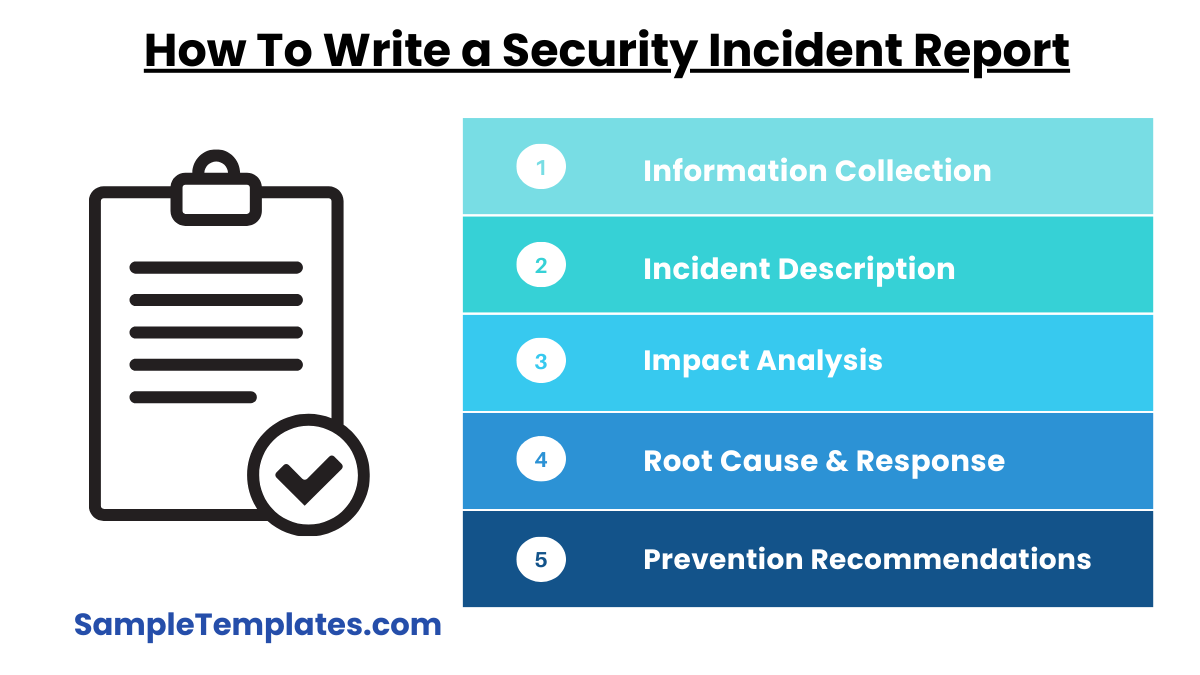
1. Collect Detailed Information
- Identify the Incident: Document the date, time, and nature of the incident. Specify what happened, where it occurred, and how it was detected.
- Gather Evidence: Collect logs, screenshots, emails, and any other relevant data that can provide context and details about the incident.
2. Describe the Incident Clearly
- Incident Summary: Write a brief summary of the incident, including key facts and immediate impact.
- Detailed Description: Provide a step-by-step account of what occurred, including the sequence of events, affected systems, and any initial responses taken.
3. Analyze the Impact
- Scope of Impact: Assess which systems, data, and operations were affected. Quantify the impact in terms of data loss, downtime, financial cost, and any legal implications.
- Business Impact: Describe how the incident affected business operations and services, including any disruptions or potential damage to the organization’s reputation. You can also see more on Security Reports.
4. Identify the Root Cause and Response
- Root Cause Analysis: Investigate and identify the underlying cause of the incident. Explain how and why it occurred, detailing any vulnerabilities or weaknesses exploited.
- Response Actions: Document the steps taken to contain, mitigate, and resolve the incident. Include both immediate and long-term actions, such as system patches, configuration changes, and any communication with stakeholders.
5. Recommend Preventive Measures
- Lessons Learned: Reflect on what was done well and what could be improved in the response process.
- Future Recommendations: Provide specific recommendations for preventing similar incidents in the future. This may include changes to security policies, additional training for staff, and enhancements to security infrastructure and monitoring systems. You can also see more on Security Incident Report Form.
Software Security Report Template

Free Security Incident Report Template

Our website offers several examples of security incident sample reports that can be used by most establishments who need to guide their security staff on procedures when filing reports. These can be downloaded and edited for specifications before printing or can be used immediately with minor modifications after printing
Security Incident Report Form
What are the Four Types of Incident Reports?
- Security Incident Reports
- Purpose: Document breaches or attacks on IT systems.
- Examples: Data breaches, malware, phishing, unauthorized access.
- Safety Incident Reports
- Purpose: Record incidents impacting individual safety.
- Examples: Workplace accidents, injuries, hazardous spills.
- Operational Incident Reports
- Purpose: Document disruptions in business operations.
- Examples: System outages, equipment failures, supply chain issues.
- Customer Incident Reports
- Purpose: Record incidents affecting customer experience.
- Examples: Customer complaints, service delivery issues, product defects.
Security Incident Report Example
Cyber Security Incident Report in PDF
Using Security Incident Reports:
Security incident reports are very important summaries of any misconduct or criminal incidents that security staff must file not just in accordance to company rules but for police authorities who need a written account of the incident for the filing of an official incident report since incident reports are used for filing of cases and insurance purposes.
When a security incident happens to involve an employee in the workplace, it constitutes a breach of rules and regulations. Such cases may either range from theft, destruction of company property, or, worse, an assault on a co-employee. Such cases still constitute a security incident and a report of the details of such violations is often requested by the employer and human resource manager. This is to determine if the violation is serious enough to warrant the firing of the offending employee. You may also see crime reports.
Aviation Security Incident Report
Tips For Creating a Security Incident Reports
- Be Objective and Factual: Stick to the facts and avoid subjective language or assumptions. Sample report only what you observed or confirmed.
- Provide Clear Descriptions: Describe the incident in detail, including the who, what, where, when, and how. Ensure the information is comprehensive and understandable.
- Include Date and Time: Record the exact date and time of the incident, as well as when the report was created. This helps establish a clear timeline.
- Document Evidence: Include any physical evidence, photographs, videos, or digital logs relevant to the incident. Ensure the evidence is securely stored and referenced in the report.
- Detail Actions Taken: Outline any immediate actions taken to address the incident, including who was notified, what steps were taken to contain the situation, and any follow-up actions.
- List Involved Parties: Provide the names and roles of all individuals involved in the incident, including witnesses, suspects, and responders.
- Use Clear Language: Write in clear, simple language, avoiding technical jargon or acronyms that may not be widely understood.
- Proofread for Accuracy: Review the report for accuracy, completeness, and clarity before submission. Ensure there are no errors or missing information.
- Follow a Standard Format: Use a standardized template or format if available, ensuring consistency and professionalism in reporting.
- Confidentiality: Maintain confidentiality and ensure the report outline is accessible only to authorized personnel. Handle sensitive information with care.
Information Security Incident Report
Campus Security Incident Report
A Security Incident Report should follow the five basics of reporting:
1. Who – The person or persons involved in the incident
2. What – Details of the incident and summary of the report. This is the most important part of the report that needs to be detailed as much as possible. Check on the incident report forms that are on the internet for more.
3. Why – Outline the circumstances of why the incident possibly happened. In this case, there may be witnesses to the incident who need to be interviewed. With the help of the incident report samples that are available online, you can make the right incident report you need for your organization.
4. When – When the incident possibly happened. Since there’s always no accurate time to verify the incident unless captured by a closed-circuit camera, the common procedure usually estimates the time closest to when the incident possibly happened based on the accounts of those involved and possible witnesses. Look at daily incident reports too.
5. How – How the incident happened based on accounts by those who saw the incident. This report may also take into account security camera footage of the security incident.
For more samples related to security filing reports, please check on our examples of sample police reports by clicking on the link which will direct you to a couple of police report examples. These are intended to be used as guides only and should not be used as official police reports after downloading.
Security Incident Report Format
Cyber Security Incident Report Format
Wrapping Up:
Security incidents not only constitute physical assaults but also cybersecurity. Our security incident report examples present a format for documenting cybersecurity incidents such as breach of systems related to sensitive information. Cybersecurity crimes have been increasing year by year and involve such incidents as lost or compromised programs and cyber espionage. The activity report samples that are on the internet can help you make the best activity reports you want to use of any kind.
Banks are particularly vulnerable to hacking incidents and need to beef up their security by upgrading their systems to prevent serious losses. You may also see management reports. We offer even more examples of Incident Report Samples that users may want to check out. These are all downloadable and printable as guides for drafting incident report samples.
General FAQs
1. What is a Security Incident Report?
A security incident report can be defined as a report that is used to keep track of the thefts/losses and any other types of security events that occur in an organization. Keeping an accurate record of security incidents is an important part of any good security management program.
2. Why are Security Incident Reports important?
Regardless of how minor the incident is, it is very important to report incidents to the company’s security team so that they can investigate the possible risks of the incident. Such reports are responsible for establishing security policies and protocols for the organization.
3. How can one identify a Security Incident?
One can identify a security incident with the help of the following:
- Unusual behavior from user accounts
- Unauthorized insider trying to access services and data
- Traffic sent to or from unidentified locations
- Excessive consumption of data
- Changes in the general configuration in the organization
- Unexpected changes in the workplace.
4. What are a few examples of Security Incidents?
There are many kinds of security incidents that make a lot of difference in the organization. Computer system breach, unauthorized access for the use of systems, theft or loss of data, equipment, etc. are a few basic examples of a security incident. Reporting these problems provides a way to monitor potential problems.
5. How is a Security Incident Report written?
You can write a security incident report with the help of the following steps:
- The date and time of the incident
- The location of the incident
- The type of incident and description of what happened
- Name the victims and their injuries, if any
- List any witnesses with their side of what has happened.
In conclusion, the incident has been documented comprehensively, and appropriate measures have been taken. Continuous monitoring and preventive actions will be implemented to avoid recurrence. Thank you for your attention to this matter
Related Posts
Business Report Samples & Templates
Survey Reports Samples & Templates
Sample Feasibility Reports
Psychological Assessment Report Samples [ Clinical, Child, Intake ]
Report Format Samples & Templates
Acknowledgement for Internship Report Samples [ Hotel, Hospital, Teaching ]
Field Trip Report Samples [ Agriculture, Educational, Environmental ]
Student Counseling Report Samples
Narrative Accomplishment Report Samples [ Science, Teacher, Reading ]
Sample Acknowledgment Report Templates
Internship Narrative Report Samples
Interview Summary Report Samples
Sample Medical Reports
Accomplishment Report Samples
Acknowledgement for Project Report Samples [ MBA, Engineering, Internship ]